tags: windows - malware analysis
Analysis of phishing attack on HalykBank customers
I presented this at 2600 Qazaqstan (December 7, 2018). You can download a sample of malware here, password: infected. Do it at your own risk!
The following e-mail with an attachment, in the form of an .iso file, was sent to the customers of HalyBank.
Title:
E-mail body:
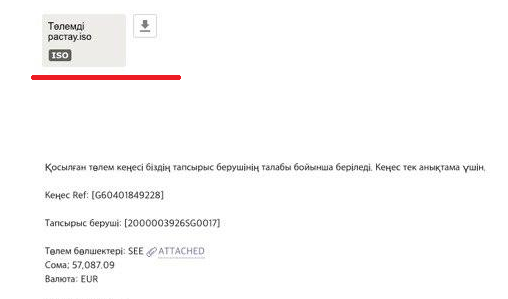
If we download the attached file, we will see that it is an .iso file, and contains Scan00987643.exe.
Why iso file? Perhaps the attackers tried to bypass the detection when running inside AV VM.
Virustotal result:
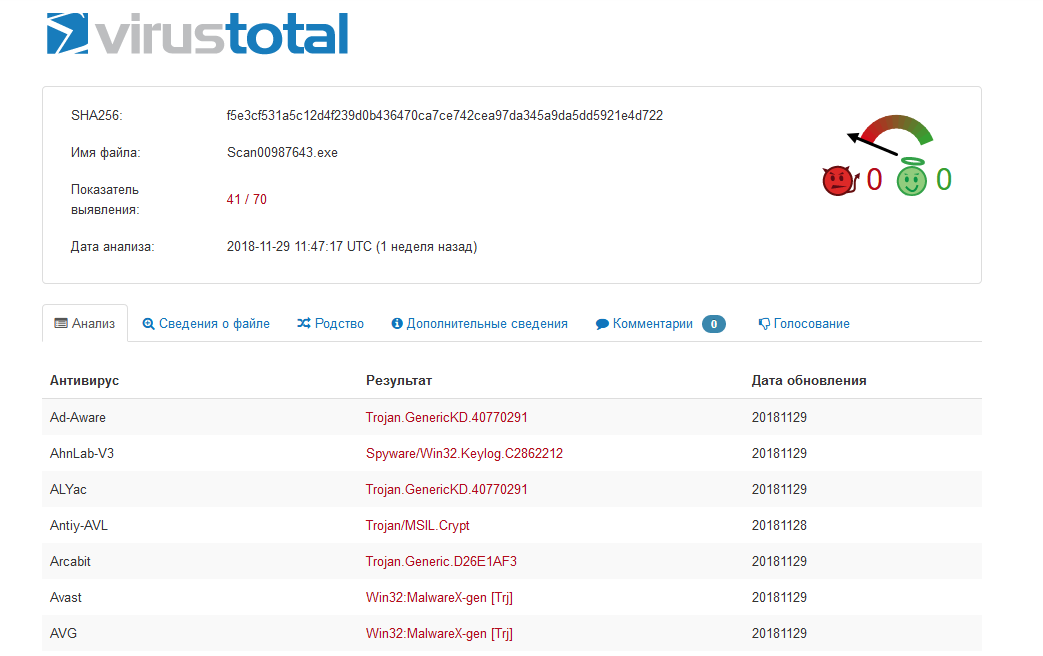
Virustotal incorrectly determined type of malware and what its code name is, lately we will see why that happened. Let’s take a closer look at the file:
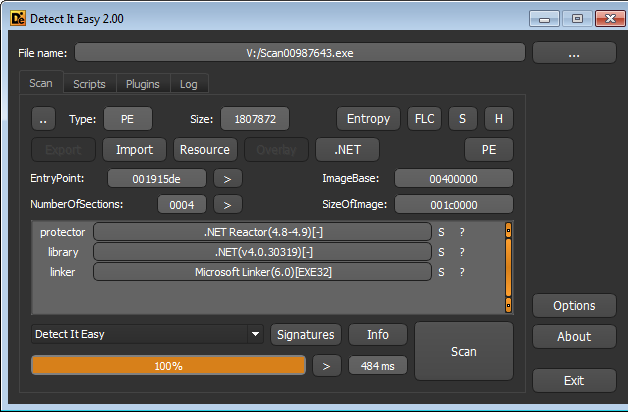
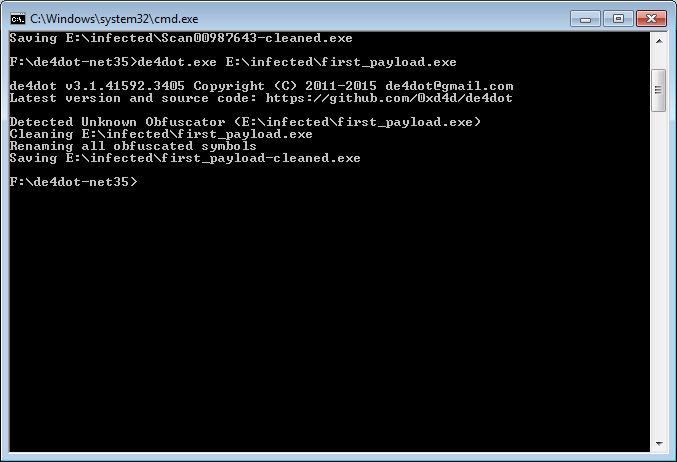
Exe is written in C#, obfuscated using .NET Reactor. We can remove obfuscation using de4dot
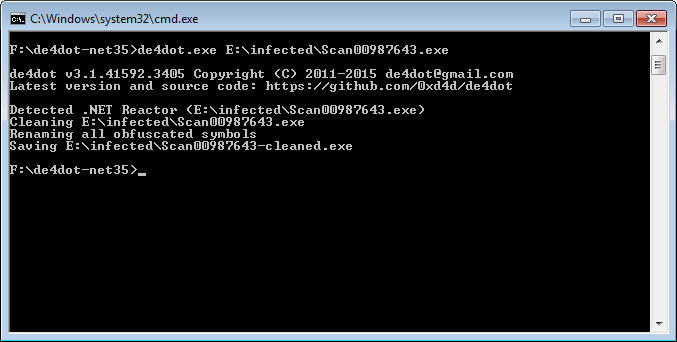
Good job! Open the cleaned file in hex editor trying to search for oddities and find such a pattern
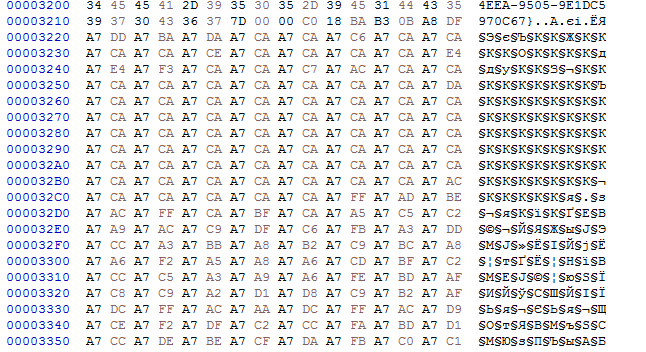
Most like xored data.
Nothing more interesting was found during the static analysis, let’s start the debugging! A great utility will help us in this - dnSpy! It is a debugger and .NET decompiler. dnSpy allows us edit application’s source code in runtime. Moreover, application can be written using the .NET Framework, .NET Core, and Unity
Having opened the exe in dnSpy, we see that it was not completely deobfuscated
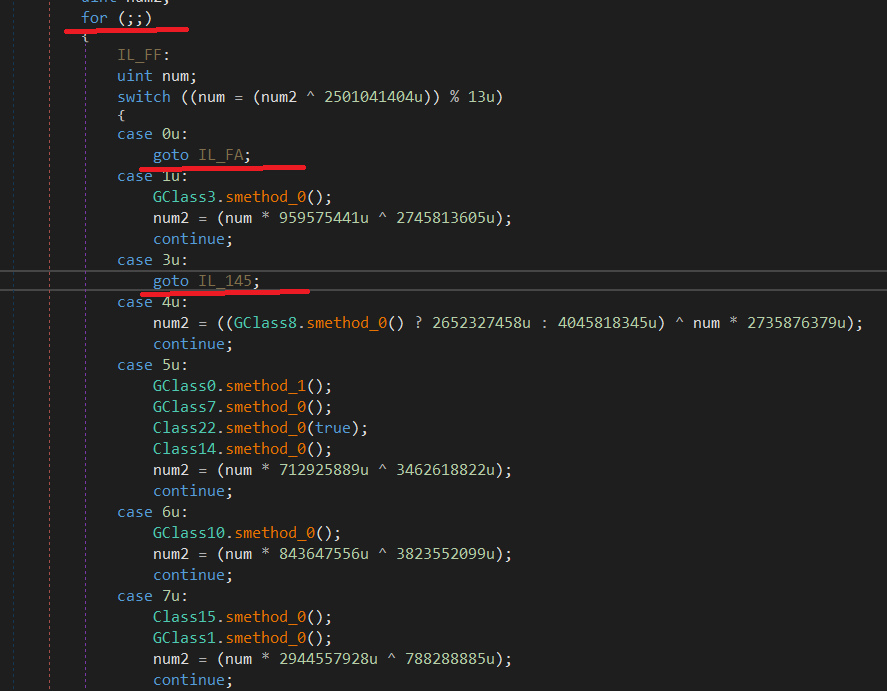
After reading the source code near the entry point, we can see that the malware loads malicious payload
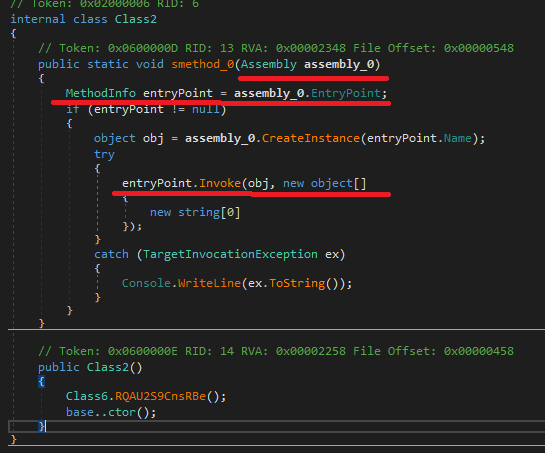
Assembly.Load() accepts a byte array with a malicious paylod. DnSpy allows us to edit source code
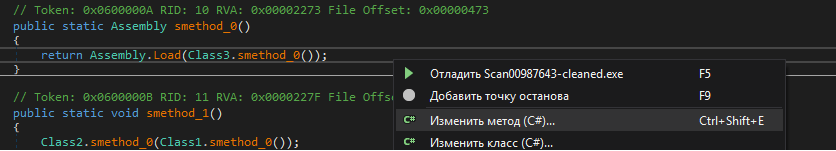
Change the payload loading so we can save it to file
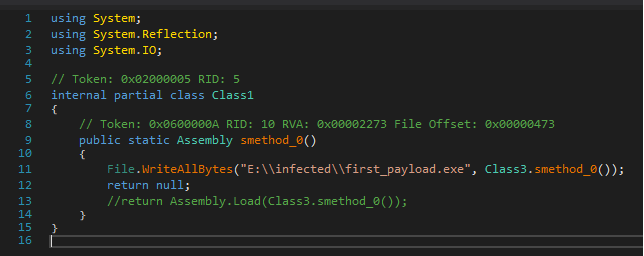
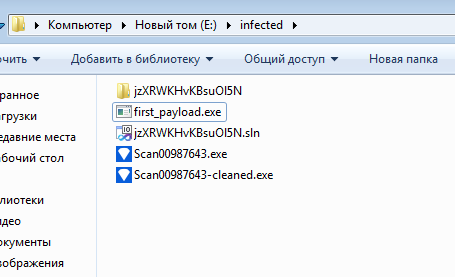
Hooray! We dumped the first payload!
Payload is also written in C# and obfuscated (DIE did not show this) * (
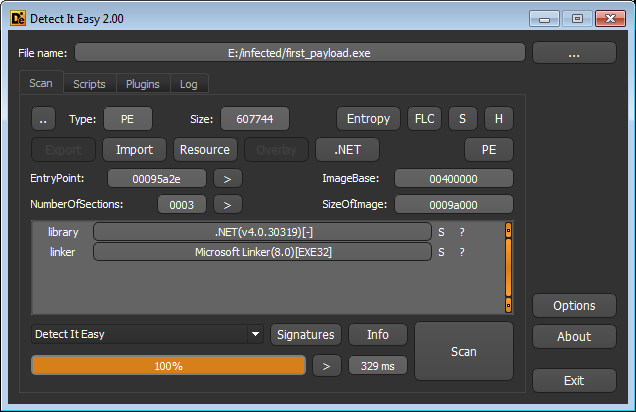
For now we have an ISO file contains an obfuscated EXE that loads another EXE, which is also obfuscated.
Use de4dot again
Load the resulting exe into dnSpy and read the source again. We see that all the strings in malware are encoded and decoded in runtime.
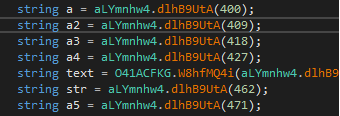
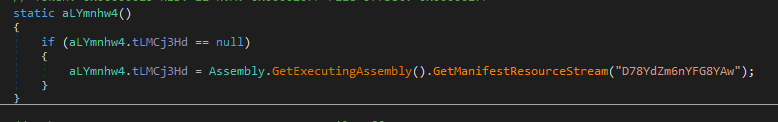
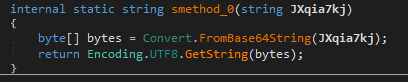
Resource section with Base64 encoded strings.
Payload copies itself to the Users folder under the name “null” and is added to autorun
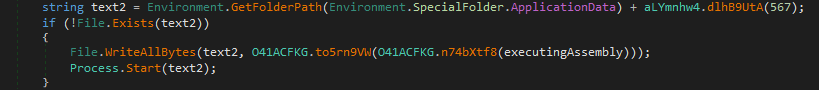
From the resources dll is loaded. DLL takes decoded exe from resource as a parameter
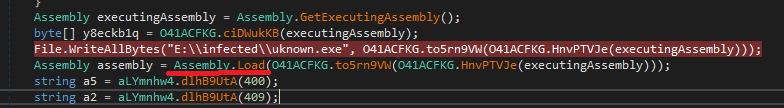
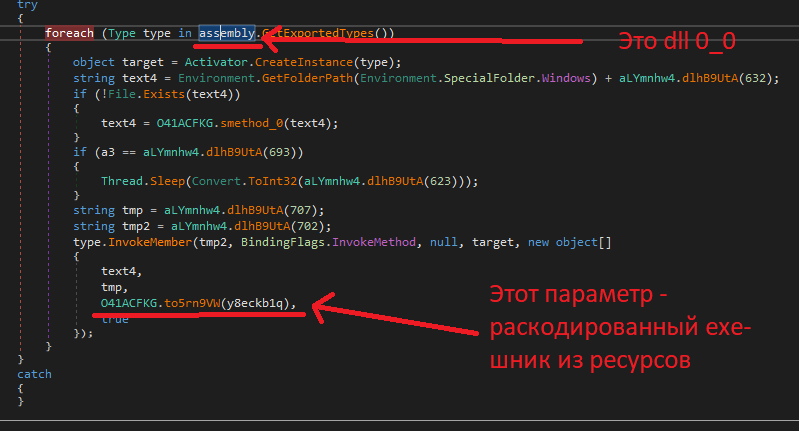
This obfuscated exe has the strange name - Reborn stub.
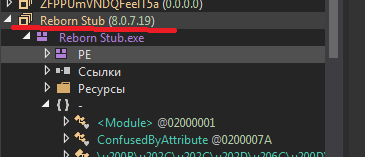
Earlier, I heard about it and therefore I decided to google this name
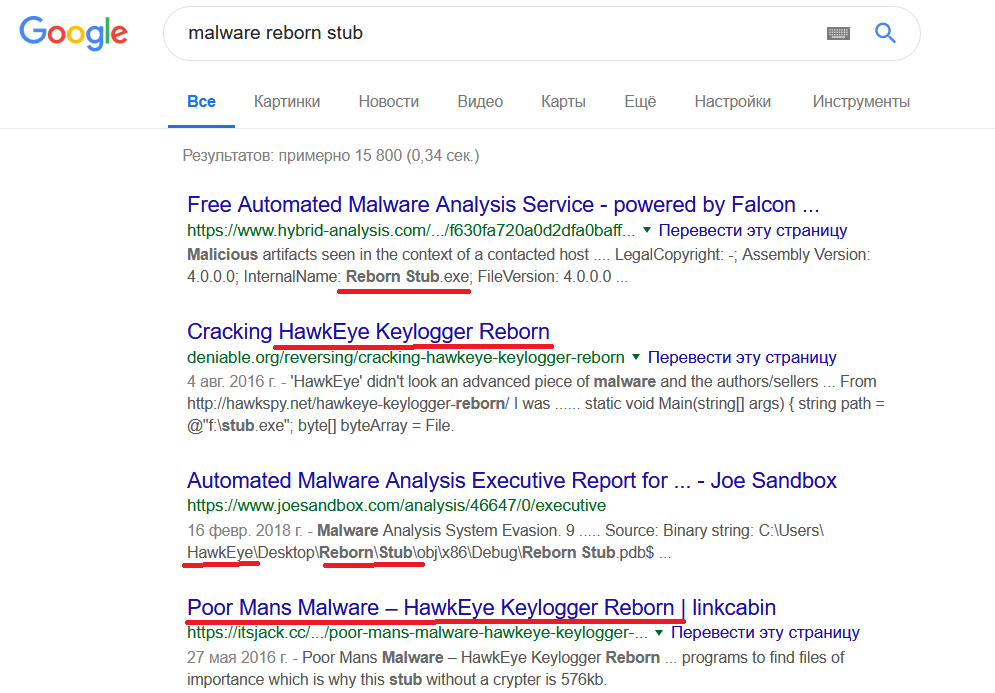
It turned out that this payload is popular Hawkeye keylogger. It was decided not to analyze further manually, but to use the any.run, for further dynamic analysis
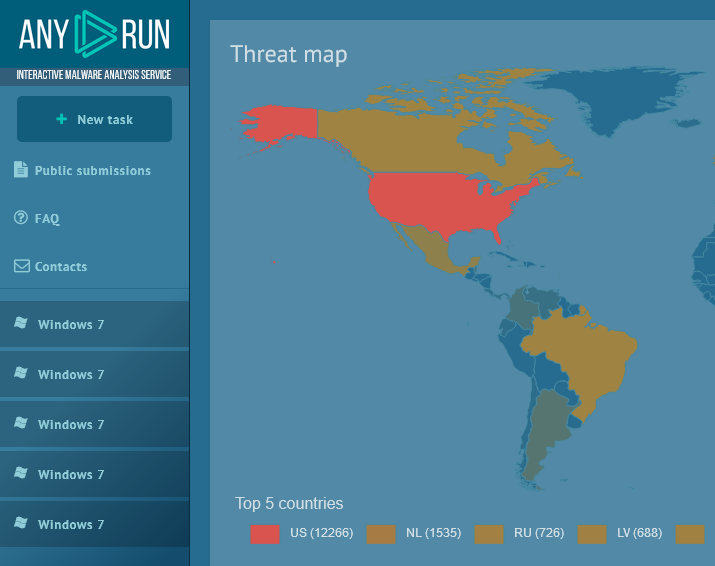
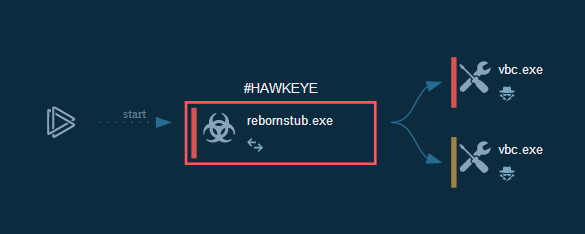
RebornStub.exe work chain
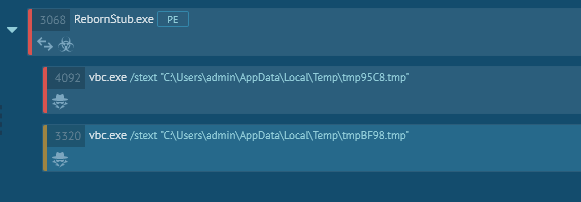
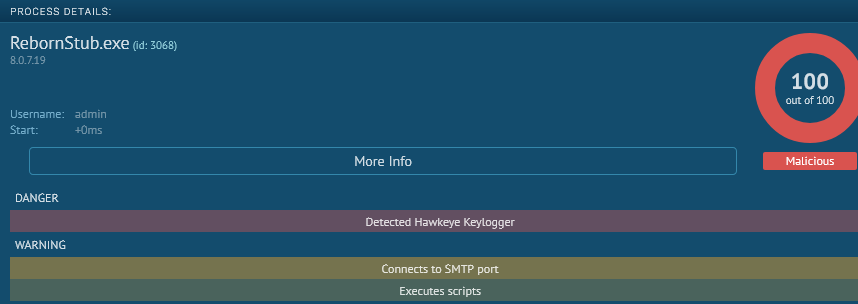
This is Hawkeye Keylogger! If you remember, initially Virustotal did not define it that way.
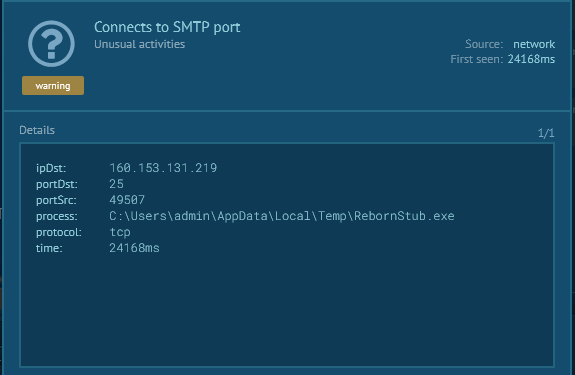
Strange outside connect
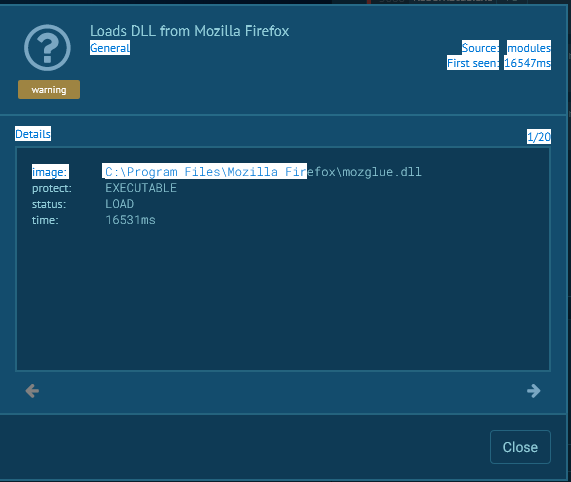
Malware loads Mozilla dll in order to steal Firefox passwords!
The general scheme